Are you struggling to remember your numerous passwords on your Macbook? savewhere.net provides a comprehensive guide to easily access, manage, and update your saved passwords. Discover effortless ways to retrieve your credentials and enhance your online security today. We’ll show you all of the latest ways to keep your accounts secured with robust passwords and passkeys.
1. Where Can I Find My Saved Passwords on My Macbook?
You can find your saved passwords on your Macbook within the Passwords app (macOS Sequoia), System Settings, or Safari. Each method offers a straightforward way to access and manage your stored credentials. Let’s break down each of these methods:
1.1. Using the Passwords App (macOS Sequoia)
If your Macbook is updated to macOS Sequoia, the Passwords app provides a dedicated and streamlined way to view your saved passwords.
Steps:
- Open the Passwords app.
- Sign in using Touch ID or your user account password.
- Select the account you want to view.
- To update, click Edit, change the password, and click Save.
- To delete, click Delete Password or Delete Passkey.
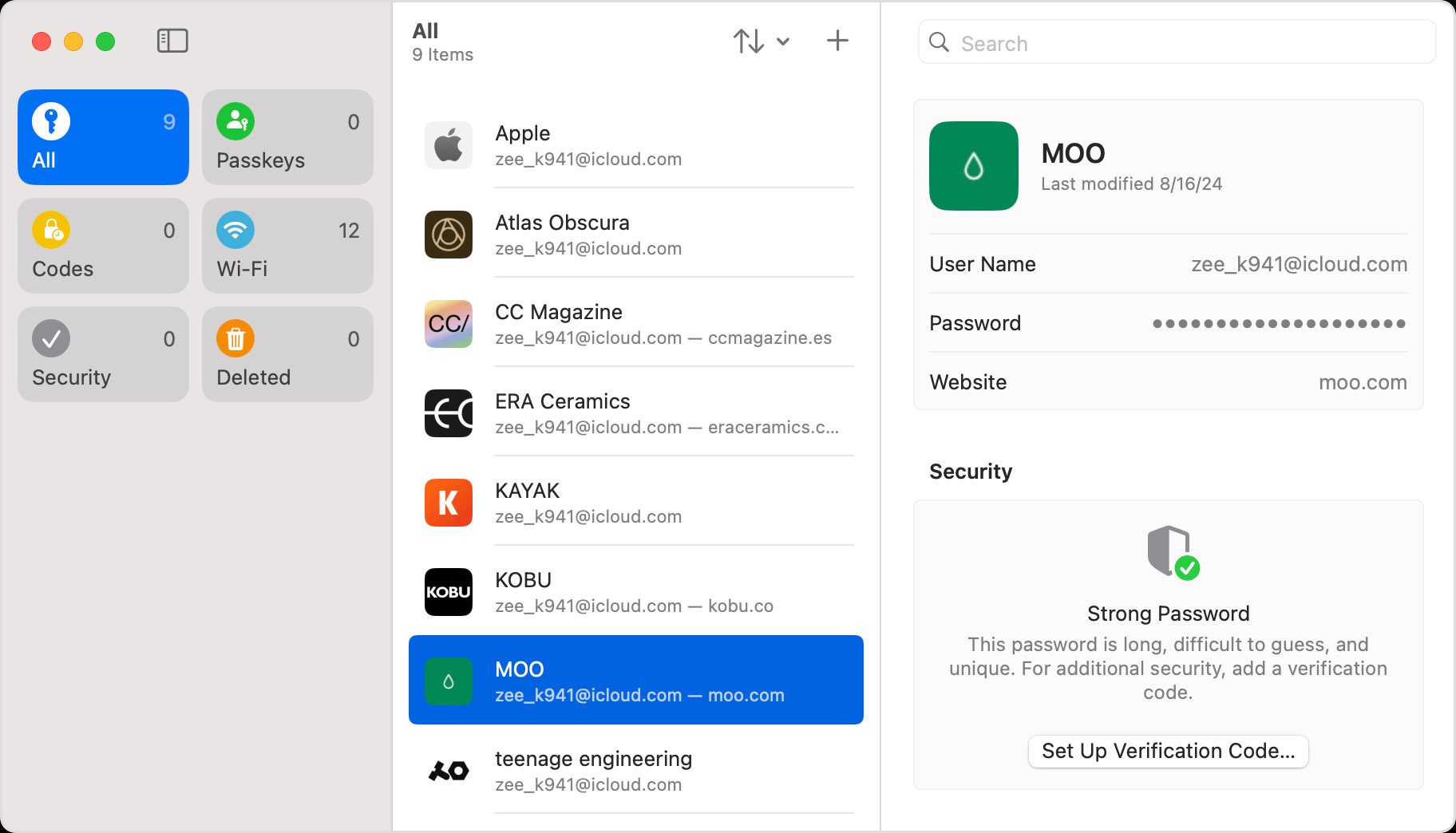 Find your saved passwords and passkeys in the Passwords app on Mac
Find your saved passwords and passkeys in the Passwords app on Mac
1.2. Accessing Passwords in System Settings (macOS Sonoma or Earlier)
For those using macOS Sonoma or earlier, accessing saved passwords through System Settings is an alternative method.
Steps:
- Click the Apple menu and go to System Settings.
- Click Passwords.
- Sign in with Touch ID or your user account password.
- Select an account, then click the Show Details button.
- To update, click Edit, change the password, and click Save.
- To delete, click Delete Password or Delete Passkey.
1.3. Viewing Passwords in Safari
Safari also provides a way to access your saved passwords directly within the browser settings.
Steps:
- Open Safari.
- From the Safari menu, choose Settings, then click Passwords.
- Sign in with Touch ID or your user account password.
- Select a website, then click the Show Details button.
- To update, click Edit, change the password, and click Save.
- To delete, click Delete Password or Delete Passkey.
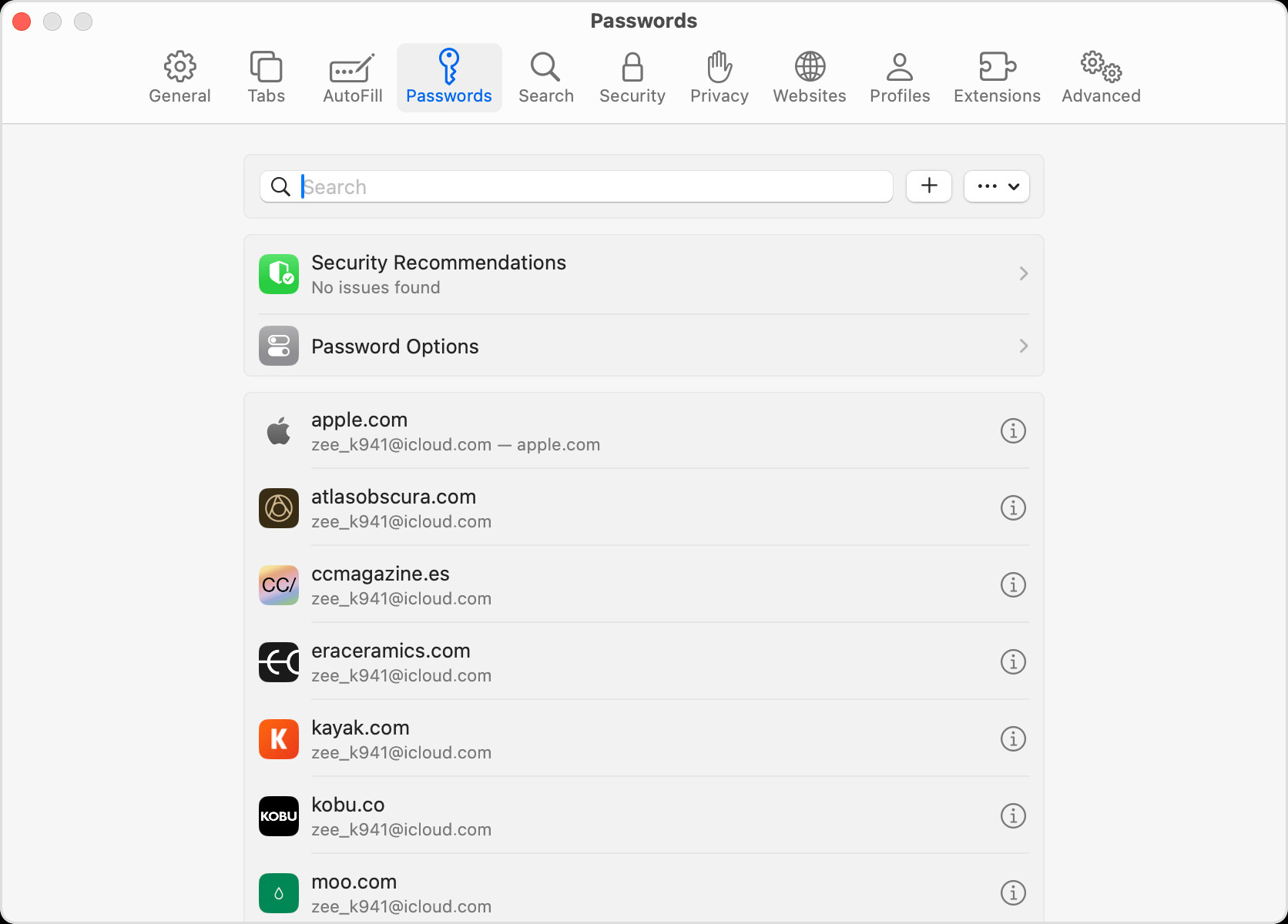 View saved passwords and passkeys in Safari Settings on macOS Sonoma or earlier
View saved passwords and passkeys in Safari Settings on macOS Sonoma or earlier
2. How Do I Use Siri to Find My Saved Passwords?
Siri can quickly show you your saved passwords with a simple voice command. Just activate Siri and say, “Show my passwords.” This convenient method provides a hands-free way to access your credentials.
3. What Should I Do If I Can’t Find A Saved Password or Passkey?
If you can’t locate a saved password or passkey, there are several troubleshooting steps you can take to resolve the issue.
3.1. Ensure You’re Viewing All Passwords
In the Passwords app, make sure that All is selected to view every stored password. Similarly, in macOS Sonoma, ensure the System Settings screen says Passwords at the top, rather than the name of a Shared Group or My Passwords.
3.2. Check Recently Deleted Passwords
Accidentally deleted a password? Check the Recently Deleted section in the Passwords app or System Settings to recover it.
Steps:
- In the Passwords app: Choose Deleted.
- In macOS Sonoma: Go to Apple menu > System Settings, click Passwords, then click Recently Deleted.
3.3. Verify iCloud Keychain is Enabled
iCloud Keychain keeps your passwords synced across all your Apple devices. Ensure it is turned on to access your passwords on your Macbook.
Steps:
- Go to System Settings.
- Click on your Apple ID.
- Select iCloud.
- Make sure Keychain is turned on.
3.4. Check Shared Groups
If you moved a password to a Shared Group, it might only be visible on devices with compatible software. Ensure your Macbook has macOS Sonoma or later to access these passwords.
4. How Does iCloud Keychain Help Manage Passwords Across Devices?
iCloud Keychain is a crucial feature that keeps your passwords, passkeys, and other secure information updated across your iPhone, iPad, iPod touch, Mac, or PC. It simplifies password management and ensures you have access to your credentials no matter which device you’re using.
According to Apple, iCloud Keychain uses AES-256 encryption to protect your passwords and credit card information. This means your data is securely stored and transmitted between your devices.
5. How Can AutoFill Help Store Credit Card Information on My Macbook?
AutoFill automatically enters your saved credit card details, contact information, and more, making online transactions quicker and easier. To set up and use AutoFill in Safari:
Steps:
- Open Safari.
- Go to Safari menu > Settings.
- Click on AutoFill.
- Configure the settings for credit cards and other information.
This feature streamlines your online experience and saves time by automatically filling in required fields.
6. What Are the Benefits of Using a Password Manager?
Using a password manager offers numerous benefits, including enhanced security, convenience, and organization. According to a study by the Ponemon Institute, organizations that use password management solutions experience a 60% reduction in the risk of data breaches. Password managers generate strong, unique passwords for each of your accounts, reducing the risk of password-related breaches. They securely store your passwords and other sensitive information, such as credit card details and personal notes.
Password managers automatically fill in your login credentials on websites and apps, saving you time and effort. Many password managers offer features like password sharing, security audits, and two-factor authentication.
7. What Should I Do If I Suspect My Password Has Been Compromised?
If you suspect your password has been compromised, take immediate action to secure your account and prevent further damage.
Steps:
- Change Your Password: Immediately change your password to a strong, unique one.
- Enable Two-Factor Authentication: Add an extra layer of security to your account by enabling two-factor authentication.
- Review Your Account Activity: Check your account activity for any unauthorized transactions or changes.
- Report the Incident: Report the incident to the service provider and relevant authorities.
7.1. Changing Your Password
When changing your password, make sure to choose a strong, unique password that is difficult to guess. A strong password should be at least 12 characters long and include a combination of uppercase and lowercase letters, numbers, and symbols.
7.2. Enabling Two-Factor Authentication
Two-factor authentication (2FA) adds an extra layer of security to your account by requiring a second verification method in addition to your password. This can be a code sent to your phone, a fingerprint scan, or a security key.
7.3. Reviewing Your Account Activity
Check your account activity for any suspicious transactions or changes. Look for unfamiliar logins, purchases, or changes to your account settings. If you notice anything unusual, report it to the service provider immediately.
7.4. Reporting the Incident
Report the incident to the service provider and relevant authorities. This will help them investigate the breach and take steps to prevent future incidents.
8. What Are Passkeys and How Do They Improve Security?
Passkeys are a more secure and convenient alternative to passwords. They use cryptographic keys to authenticate your identity, eliminating the need to remember and enter passwords. According to the FIDO Alliance, passkeys are resistant to phishing attacks and other common password-related threats.
With passkeys, you log in using biometrics (fingerprint or facial recognition) or a device PIN, making the process faster and more secure.
8.1. How Passkeys Work
Passkeys work by creating a unique cryptographic key pair for each account. One key is stored on your device, and the other is stored on the service provider’s server. When you log in, your device uses its key to prove your identity to the server.
8.2. Benefits of Passkeys
Passkeys offer several benefits over passwords, including:
- Enhanced Security: Passkeys are resistant to phishing attacks and other common password-related threats.
- Convenience: Passkeys eliminate the need to remember and enter passwords.
- Cross-Platform Compatibility: Passkeys work on a variety of devices and platforms.
9. How Can I Create Strong and Unique Passwords?
Creating strong and unique passwords is essential for protecting your online accounts from unauthorized access. A strong password should be at least 12 characters long and include a combination of uppercase and lowercase letters, numbers, and symbols.
9.1. Tips for Creating Strong Passwords
- Use a Password Generator: Use a password generator to create random, strong passwords.
- Avoid Personal Information: Do not use personal information such as your name, birthday, or address in your passwords.
- Use a Variety of Characters: Include a combination of uppercase and lowercase letters, numbers, and symbols in your passwords.
- Do Not Reuse Passwords: Do not reuse the same password for multiple accounts.
9.2. Password Length
A longer password is more difficult to crack. Aim for a password that is at least 12 characters long.
9.3. Password Complexity
A complex password includes a combination of uppercase and lowercase letters, numbers, and symbols. This makes it more difficult for hackers to guess or crack your password.
9.4. Password Uniqueness
Do not reuse the same password for multiple accounts. If one of your passwords is compromised, hackers could use it to access your other accounts.
10. What Are Some Common Password Security Mistakes to Avoid?
Avoiding common password security mistakes can significantly improve your online security.
10.1. Using Weak Passwords
Using weak passwords that are easy to guess is a common mistake. Avoid using personal information, common words, or simple patterns in your passwords.
10.2. Reusing Passwords
Reusing the same password for multiple accounts is another common mistake. If one of your passwords is compromised, hackers could use it to access your other accounts.
10.3. Sharing Passwords
Sharing your passwords with others can put your accounts at risk. Avoid sharing your passwords with anyone, including family members and friends.
10.4. Storing Passwords Insecurely
Storing your passwords in plain text on your computer or in a note is not secure. Use a password manager to securely store your passwords.
11. How Can I Protect My Macbook From Malware and Phishing Attacks?
Protecting your Macbook from malware and phishing attacks is essential for maintaining your online security.
11.1. Install Antivirus Software
Install antivirus software and keep it up to date. Antivirus software can detect and remove malware from your computer.
11.2. Be Careful About Clicking Links
Be careful about clicking links in emails and on websites. Phishing attacks often use fake links to trick you into entering your login credentials.
11.3. Keep Your Software Up to Date
Keep your software up to date. Software updates often include security patches that can protect your computer from malware and phishing attacks.
11.4. Use a Firewall
Use a firewall to block unauthorized access to your computer. A firewall can prevent hackers from accessing your computer and stealing your data.
12. How Does Biometric Authentication Enhance Security on Macbooks?
Biometric authentication uses unique biological traits, such as fingerprints or facial recognition, to verify your identity. This adds an extra layer of security to your Macbook and makes it more difficult for unauthorized users to access your device.
12.1. Fingerprint Scanning
Fingerprint scanning uses a fingerprint sensor to verify your identity. This is a convenient and secure way to log in to your Macbook and authorize transactions.
12.2. Facial Recognition
Facial recognition uses a camera to scan your face and verify your identity. This is another convenient and secure way to log in to your Macbook and authorize transactions.
13. What Role Does Encryption Play in Protecting Saved Passwords?
Encryption plays a crucial role in protecting saved passwords by scrambling your data into an unreadable format. This prevents unauthorized users from accessing your passwords, even if they gain access to your computer or password database.
13.1. Types of Encryption
There are several types of encryption, including:
- AES (Advanced Encryption Standard): A widely used encryption algorithm that is considered to be very secure.
- RSA (Rivest-Shamir-Adleman): A public-key encryption algorithm that is used to secure data transmissions.
- SSL/TLS (Secure Sockets Layer/Transport Layer Security): A protocol that is used to encrypt communications between your computer and a website.
13.2. Encryption in Password Managers
Password managers use encryption to protect your saved passwords. When you save a password in a password manager, it is encrypted using a strong encryption algorithm. This ensures that your passwords are protected from unauthorized access.
14. How Can Regular Password Audits Improve My Online Security?
Regular password audits can help you identify weak or compromised passwords and take steps to improve your online security.
14.1. Identifying Weak Passwords
A password audit can help you identify weak passwords that are easy to guess. This includes passwords that are short, contain personal information, or use common words.
14.2. Identifying Reused Passwords
A password audit can also help you identify reused passwords. Reusing the same password for multiple accounts is a security risk. If one of your passwords is compromised, hackers could use it to access your other accounts.
14.3. Changing Weak and Reused Passwords
Once you have identified weak and reused passwords, you should change them to strong, unique passwords. This will help improve your online security and protect your accounts from unauthorized access.
15. What Resources Are Available for Staying Updated on Password Security Best Practices?
Staying updated on password security best practices is essential for protecting your online accounts from unauthorized access.
15.1. Security Blogs and Websites
Follow security blogs and websites to stay updated on the latest password security threats and best practices.
15.2. Security Newsletters
Subscribe to security newsletters to receive regular updates on password security topics.
15.3. Security Conferences
Attend security conferences to learn from experts and network with other security professionals.
15.4. Government Resources
Refer to government resources such as the National Institute of Standards and Technology (NIST) for password security guidelines.
16. How To Choose The Right Password Manager?
Choosing the right password manager is crucial for securing your online credentials effectively. With a plethora of options available, each offering unique features and benefits, it’s important to consider several key factors before making a decision.
16.1. Security Features
Ensure the password manager employs robust encryption methods, such as AES-256, to protect your data both in transit and at rest. Look for features like two-factor authentication (2FA) for added security, as well as biometric authentication options such as fingerprint or facial recognition.
16.2. User Interface and Experience
Opt for a password manager with a user-friendly interface that is easy to navigate and understand. The software should offer seamless integration with your web browsers and devices, allowing for convenient password storage and retrieval.
16.3. Device Compatibility
Verify that the password manager supports all of your devices, including desktops, laptops, smartphones, and tablets. Cross-platform compatibility ensures that you can access your passwords from anywhere, at any time.
16.4. Additional Features
Consider whether the password manager offers additional features that align with your needs, such as password generation, secure notes, identity theft protection, and password sharing. Evaluate the value of these features and whether they justify the cost of the subscription.
16.5. Cost and Subscription Plans
Compare the pricing models of different password managers, including monthly or annual subscription plans, as well as any free options. Determine whether the features offered in the paid plans justify the additional cost, and consider whether a free version meets your basic password management needs.
17. What Are The Most Common Types Of Phishing Scams?
Recognizing the various forms of phishing scams is crucial for preventing online fraud and identity theft. Phishing attacks often masquerade as legitimate communications from trusted sources, making it essential to stay vigilant and informed.
17.1. Email Phishing
Email phishing is one of the most common types of phishing scams, where attackers send fraudulent emails that appear to be from reputable companies or organizations. These emails often contain malicious links or attachments designed to steal your login credentials or install malware on your device.
17.2. Spear Phishing
Spear phishing is a targeted form of phishing where attackers personalize their emails to specific individuals or organizations. These emails often contain detailed information about the recipient, making them more convincing and harder to detect.
17.3. Whaling
Whaling is a type of spear phishing that targets high-profile individuals, such as executives or celebrities. These attacks are often highly sophisticated and aim to steal sensitive information or gain access to valuable assets.
17.4. Smishing
Smishing is a type of phishing that uses SMS text messages to trick victims into revealing their personal information. These messages often contain links to fake websites or ask you to call a fraudulent phone number.
17.5. Vishing
Vishing, or voice phishing, involves attackers using phone calls to deceive victims into providing their personal or financial information. These calls often impersonate legitimate organizations, such as banks or government agencies.
18. How To Identify A Phishing Email?
Identifying phishing emails is crucial for protecting yourself from online scams and identity theft. By recognizing the common signs of phishing, you can avoid falling victim to fraudulent schemes and safeguard your personal information.
18.1. Generic Greetings
Phishing emails often use generic greetings such as “Dear Customer” or “Dear Account Holder” instead of addressing you by name.
18.2. Spelling and Grammar Errors
Phishing emails often contain spelling and grammar errors, as scammers may not have strong language skills or may intentionally include errors to evade spam filters.
18.3. Suspicious Links
Phishing emails often contain links to fake websites that look similar to legitimate ones. Always hover over links before clicking to verify that they lead to the correct destination.
18.4. Urgent Requests
Phishing emails often create a sense of urgency by threatening to close your account or impose fees if you don’t take immediate action.
18.5. Unsolicited Requests for Personal Information
Legitimate organizations will never ask you to provide sensitive information such as passwords, social security numbers, or credit card details via email.
19. What Are The Best Ways To Back Up My Passwords?
Backing up your passwords is a crucial step in ensuring that you don’t lose access to your online accounts. Whether you’re using a password manager or storing your passwords manually, having a backup plan in place can save you from a lot of headaches down the road.
19.1. Export Passwords From Password Manager
Most password managers offer the option to export your passwords to a file, such as a CSV or TXT file. This allows you to create a backup of your passwords that you can store securely.
19.2. Store Backup File Securely
When backing up your passwords, it’s important to store the backup file securely to prevent unauthorized access. Consider encrypting the file with a strong password and storing it on an external hard drive or USB drive that you keep in a safe place.
19.3. Cloud Backup
Some password managers also offer the option to back up your passwords to the cloud. This can be a convenient way to ensure that your passwords are always backed up, but it’s important to choose a password manager that uses strong encryption to protect your data in the cloud.
19.4. Print Out Passwords
While not the most secure option, printing out your passwords and storing them in a safe place can be a backup in case of emergencies. Be sure to keep the printed list in a secure location where it won’t be easily accessible to others.
19.5. Regularly Update Backups
It’s important to regularly update your password backups to ensure that they contain the most up-to-date information. Set a reminder to back up your passwords at least once a month, or more frequently if you make frequent changes to your passwords.
20. How Can I Protect My Credit Card Information Online?
Protecting your credit card information online is essential to prevent fraud and identity theft. With the rise of e-commerce, it’s more important than ever to take precautions when making online purchases.
20.1. Shop at Secure Websites
Always shop at websites that use SSL (Secure Sockets Layer) encryption to protect your credit card information. Look for the padlock icon in the address bar and make sure the website’s URL starts with “https://”.
20.2. Use Strong Passwords
Use strong, unique passwords for your online accounts to prevent hackers from gaining access to your credit card information.
20.3. Monitor Your Accounts Regularly
Regularly monitor your bank and credit card statements for any unauthorized transactions. If you notice any suspicious activity, report it to your bank or credit card company immediately.
20.4. Use a Credit Card With Fraud Protection
Choose a credit card that offers fraud protection and zero liability for unauthorized transactions. This will help protect you from financial losses if your credit card information is stolen.
20.5. Be Wary of Phishing Scams
Be wary of phishing scams that attempt to trick you into providing your credit card information. Never click on links in suspicious emails or text messages, and always verify the legitimacy of a website before entering your credit card details.
21. What Are The Risks Of Public Wi-Fi Networks?
Public Wi-Fi networks can be convenient, but they also pose several security risks. When using public Wi-Fi, your data can be vulnerable to eavesdropping and hacking.
21.1. Unencrypted Connections
Most public Wi-Fi networks do not use encryption, which means that your data is transmitted in plain text and can be easily intercepted by hackers.
21.2. Man-in-the-Middle Attacks
Hackers can set up fake Wi-Fi hotspots that look like legitimate public networks. When you connect to these fake hotspots, your data can be intercepted and stolen.
21.3. Malware Distribution
Public Wi-Fi networks can be used to distribute malware. Hackers can inject malicious code into websites that you visit, which can then infect your device.
21.4. Eavesdropping
Hackers can use packet sniffers to eavesdrop on your internet traffic and steal your login credentials, credit card numbers, and other sensitive information.
21.5. Lack of Security Protocols
Public Wi-Fi networks often lack basic security protocols, such as firewalls and intrusion detection systems, which makes them more vulnerable to attack.
22. How Can I Secure My Macbook When Using Public Wi-Fi?
Securing your Macbook when using public Wi-Fi is essential to protect your data from hackers and eavesdroppers.
22.1. Use a VPN
A Virtual Private Network (VPN) encrypts your internet traffic and routes it through a secure server, which makes it more difficult for hackers to intercept your data.
22.2. Use HTTPS
Only visit websites that use HTTPS (Hypertext Transfer Protocol Secure) encryption to protect your data. Look for the padlock icon in the address bar and make sure the website’s URL starts with “https://”.
22.3. Turn Off File Sharing
Turn off file sharing to prevent others from accessing your files over the public Wi-Fi network.
22.4. Enable Firewall
Enable the firewall on your Macbook to block unauthorized access to your device.
22.5. Use Two-Factor Authentication
Use two-factor authentication (2FA) for your online accounts to add an extra layer of security. This requires you to enter a code from your phone or another device in addition to your password when logging in.
23. How To Manage Social Media Passwords Securely?
Managing social media passwords securely is crucial, given the amount of personal information stored on these platforms.
23.1. Use Strong Passwords
Create strong, unique passwords for each of your social media accounts. Avoid using the same password for multiple accounts.
23.2. Use a Password Manager
Use a password manager to securely store your social media passwords and generate strong passwords for you.
23.3. Enable Two-Factor Authentication
Enable two-factor authentication (2FA) for your social media accounts to add an extra layer of security. This requires you to enter a code from your phone or another device in addition to your password when logging in.
23.4. Review Third-Party Apps
Regularly review the third-party apps that have access to your social media accounts and remove any that you no longer use.
23.5. Be Wary of Phishing Scams
Be wary of phishing scams that attempt to trick you into providing your social media login credentials. Never click on links in suspicious emails or text messages, and always verify the legitimacy of a website before entering your login details.
24. What Are The Signs Of Identity Theft?
Recognizing the signs of identity theft is crucial for taking prompt action to protect your personal information and financial assets.
24.1. Unauthorized Transactions
Look for unauthorized transactions on your bank and credit card statements.
24.2. Missing Bills
Be alert for missing bills or statements, which could indicate that someone has changed your mailing address.
24.3. Unknown Accounts
Watch for unknown accounts or credit cards on your credit report.
24.4. Debt Collection Calls
Beware of debt collection calls for debts that you don’t recognize.
24.5. Denied Credit
Take note if you are denied credit for no apparent reason.
25. What Should I Do If I Become A Victim Of Identity Theft?
If you become a victim of identity theft, it’s important to take immediate action to minimize the damage and protect your financial future.
25.1. File a Police Report
File a police report to document the identity theft and provide evidence for your claims.
25.2. Contact Your Bank and Credit Card Companies
Contact your bank and credit card companies to report the identity theft and cancel any unauthorized transactions.
25.3. Place a Fraud Alert on Your Credit Reports
Place a fraud alert on your credit reports to warn creditors that you may be a victim of identity theft.
25.4. Review Your Credit Reports
Review your credit reports from all three major credit bureaus (Equifax, Experian, and TransUnion) for any signs of fraud.
25.5. File a Complaint With The FTC
File a complaint with the Federal Trade Commission (FTC) to report the identity theft and provide information for their investigations.
26. How Does The U.S. Bureau of Economic Analysis (BEA) Contribute To Financial Security?
The U.S. Bureau of Economic Analysis (BEA) plays a vital role in contributing to financial security by providing accurate and reliable economic data that informs policy decisions and helps individuals and businesses make sound financial choices. According to research from the U.S. Bureau of Economic Analysis (BEA), in July 2025, consumer spending increased by 0.8%, indicating a strong and resilient economy.
26.1. Economic Data
The BEA collects and publishes a wide range of economic data, including GDP (Gross Domestic Product), personal income, and consumer spending. This data provides insights into the health of the economy and helps policymakers make informed decisions about fiscal and monetary policy.
26.2. Policy Decisions
The economic data provided by the BEA is used by policymakers to make decisions about interest rates, government spending, and tax policies. These decisions can have a significant impact on financial security and economic growth.
26.3. Financial Choices
Individuals and businesses can use the economic data provided by the BEA to make informed financial choices. For example, they can use GDP data to assess the strength of the economy and make decisions about investing and spending.
26.4. Economic Growth
By providing accurate and reliable economic data, the BEA helps promote economic growth and stability, which are essential for financial security.
27. How Can The Consumer Financial Protection Bureau (CFPB) Help Me With Financial Security?
The Consumer Financial Protection Bureau (CFPB) is a U.S. government agency that protects consumers from financial fraud and abuse. The CFPB provides a variety of resources and tools to help consumers make informed financial decisions and protect their financial security.
27.1. Financial Fraud and Abuse
The CFPB investigates and takes action against companies that engage in financial fraud and abuse.
27.2. Resources and Tools
The CFPB provides a variety of resources and tools to help consumers make informed financial decisions. These include educational materials, calculators, and complaint forms.
27.3. Financial Security
By protecting consumers from financial fraud and abuse, the CFPB helps promote financial security and economic stability.
27.4. Complaint Forms
Consumers can file complaints with the CFPB if they have been victims of financial fraud or abuse. The CFPB will investigate these complaints and take action against companies that violate consumer protection laws.
28. What Are The Latest Trends In Password Management?
Staying informed about the latest trends in password management is crucial for maintaining strong online security.
28.1. Passwordless Authentication
Passwordless authentication is a trend that eliminates the need for passwords altogether. Instead, users log in using biometrics, such as fingerprint or facial recognition, or other authentication methods.
28.2. Passkeys
Passkeys are a new technology that uses cryptographic keys to authenticate users. They are more secure and convenient than passwords and are resistant to phishing attacks.
28.3. Biometric Authentication
Biometric authentication, such as fingerprint and facial recognition, is becoming increasingly popular for password management. It provides a convenient and secure way to log in to your online accounts.
28.4. Adaptive Authentication
Adaptive authentication uses machine learning to analyze user behavior and assess the risk of a login attempt. If the risk is high, the user may be required to provide additional authentication factors.
28.5. Cloud-Based Password Management
Cloud-based password management allows users to securely store and access their passwords from any device. This is convenient for users who have multiple devices and need to access their passwords on the go.
29. What Are The Best Practices For Mobile Password Security?
Mobile devices are increasingly used for accessing online accounts, making mobile password security more important than ever.
29.1. Use Strong Passwords
Create strong, unique passwords for each of your mobile accounts. Avoid using the same password for multiple accounts.
29.2. Use a Password Manager
Use a password manager to securely store your mobile passwords and generate strong passwords for you.
29.3. Enable Biometric Authentication
Enable biometric authentication, such as fingerprint or facial recognition, on your mobile device to add an extra layer of security.
29.4. Use a PIN or Password Lock
Use a PIN or password lock on your mobile device to prevent unauthorized access.
29.5. Keep Your Software Up To Date
Keep your mobile operating system and apps up to date to ensure that you have the latest security patches.
30. How Can I Stay Safe From Keyloggers On My Macbook?
Keyloggers are malicious software that record your keystrokes, allowing hackers to steal your passwords and other sensitive information.
30.1. Install Antivirus Software
Install antivirus software and keep it up to date. Antivirus software can detect and remove keyloggers from your computer.
30.2. Be Careful About Clicking Links
Be careful about clicking links in emails and on websites. Phishing attacks often use fake links to trick you into downloading keyloggers.
30.3. Use a Firewall
Use a firewall to block unauthorized access to your computer. A firewall can prevent hackers from installing keyloggers on your device.
30.4. Use Two-Factor Authentication
Use two-factor authentication (2FA) for your online accounts to add an extra layer of security. This requires you to enter a code from your phone or another device in addition to your password when logging in.
30.5. Use a Virtual Keyboard
Use a virtual keyboard to enter your passwords and other sensitive information. This prevents keyloggers from recording your keystrokes.
31. What Are The Legal Implications Of Password Security Breaches?
Password security breaches can have significant legal implications for both individuals and organizations.
31.1. Data Breach Notification Laws
Data breach notification laws require organizations to notify individuals if their personal information has been compromised in a security breach.
31.2. Liability for Damages
Organizations can be held liable for damages resulting from password security breaches, such as financial losses and identity theft.
31.3. Regulatory Fines
Organizations that violate data protection laws can face regulatory fines and penalties.
31.4. Criminal Charges
Individuals who engage in hacking and password theft can face criminal charges and imprisonment.
31.5. Legal Action
Individuals who have been victims of password security breaches can take legal action against organizations that failed to protect their personal information.
32. FAQ: How to Check Saved Passwords on Macbook
Here are some frequently asked questions about how to check saved passwords on your Macbook:
-
Question: How do I find my saved passwords on my Macbook?
Answer: You can find your saved passwords using the Passwords app (macOS Sequoia), System Settings (macOS Sonoma or earlier), or Safari settings. -
Question: Can I use Siri to find my saved passwords?
Answer: Yes, you can ask Siri to show your passwords by saying, “Show my passwords.” -
Question: What should I do if I can’t find a specific saved password?
Answer: Make sure you are viewing all passwords, check the Recently Deleted section, and verify that iCloud Keychain is enabled. -
Question: How does iCloud Keychain help with password management?
Answer: iCloud Keychain keeps your passwords synced across all your Apple devices, making it easier to access them from anywhere. -
Question: How can AutoFill help store credit card information on my Macbook?
Answer: AutoFill automatically enters your saved credit card details and contact information, making online transactions quicker and easier. -
Question: What are the benefits of using a password manager?
Answer: Password managers enhance security by generating strong, unique passwords and securely storing them. -
Question: What should I do if I suspect my password has been compromised?
Answer: Immediately change your password, enable two-factor authentication, and review your account activity. -
Question: What are passkeys and how do they improve security?
Answer: Passkeys are a more secure alternative to passwords that use cryptographic keys for authentication. -
Question: How can I create strong and unique passwords?
Answer: Use a password generator, avoid personal information, and use a variety of characters. -
Question: What are some common password security mistakes to avoid?
Answer: Avoid using weak passwords, reusing passwords, and sharing passwords with others.
Final Thoughts
Navigating the digital landscape requires robust password management practices. By following these guidelines, you can safeguard your online accounts, protect your financial information, and enjoy a more secure online experience. For more tips and resources on how to save money

